The USABLE project is built around a core commitment to listen - to users, to trainers, and to our partners. As we began assembling the team of amazing designers and usability experts we are working with, a common thread emerged around a desire to connect and frame their inputs as usability experts for the digital security space and map out how they would engage during the tool feedback trainings.
We were able to bring together a Security and Design Workshop in mid November, thanks to the amazing generosity and flexibility of our partners and hosted in ThoughtWorks’ new San Francisco offices. This gave the USABLE team a chance to go over operational security concerns for working with vulnerable populations and let the designers experience firsthand both some of the digital security tools we hope to work with, and the process of a digital security training. More importantly, however, was the chance to really dig in to our plans for integrating need-finding and human centered design into the digital security training process to create the “Tool Feedback Trainings” (TFTs) we envision.
For needfinding, USABLE is integrating core aspects of the SecondMuse’s Internet Freedom Need Finding Toolkit into this process to supplement our pre-training interview and engagement processes with our local partners and trainers. Members from the SecondMuse team were able to join us and help us work through their framework and adapt it to the Tool Feedback Training model in USABLE. This helped us discover what information is valuable to match a community with a tool developer, as well as understanding the threats and capacity of each community that goes into digital security trainings.
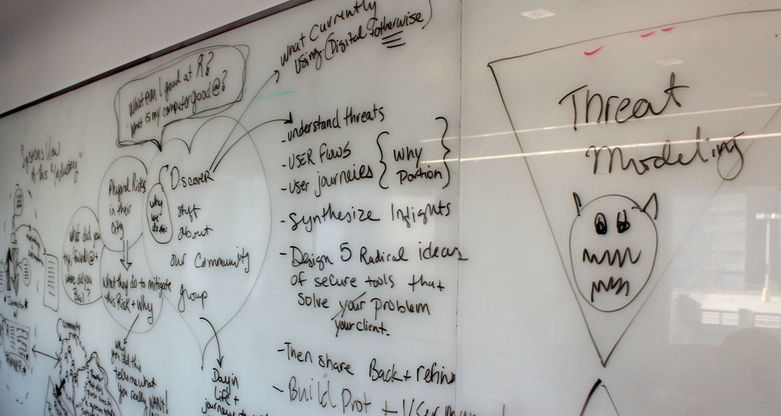
For the rest of the workshop, we worked on integrating HCD practices into the training process. The final day began with a series of human centered design exercises led by ThoughtWorks that would be adaptable for the TFT scenarios, from introductory exercises to more practical ones, such as having participants design the training or manual for a tool as a way to focus the tool’s actual interface on those aspects that truly require training, as opposed to those which could be set to secure defaults, automated, or provided as “advanced” options.
Learnings
Blending training with design
Our initial vision for the TFT schedule was an approach that bookended a more traditional digital security training with a pre- and post- session on design. During the Workshop, it became clear that a fully integrated approach where design aspects were combined into the flow of the training would be much more effective. We did a test-run of this which we’ll detail in a future blog.
Building respectful, useful Personas
Another core learning from the Workshop was around the generation of the personas, and how to present this exercise in the TFTs in a way that respects the individuality of the participants while balancing the value of a cohesive, representative persona that has utility for developers. This will not only lead to stronger outcomes, but will provide clearer representation for niche needs and barriers that sub groups of each community might have.
Unexpected outcomes are exciting
Design exercises, even short, open-ended ones like the “5 ideas” aspect of the Wallet Exercise can also be conducted even without a specific tool in mind, as a way to enable participants to design ideal theoretical tools for themselves (through a process of interviews, risk discussions, and talking about current practices). This helps the participants and facilitators understand the community’s approach to and tolerance of risk and can reveal hidden barriers to tool adoption (such as remote connectivity, battery consumption).
This process can also turn up local innovations to mitigate risks, and even expose gaps where no current tools are available to meet a need.
Finally, this provides a rare security training exercise with no “wrong” answers.
How usable is too usable?
We also wrestled with some powerful questions that could help change discussions around the pushback against some tool usability. A classic debate has been balancing making specific complex tools easier against removing some of the deeper understanding that the users are expected to learn before using them. In response to this, ThoughtWorks’ design lead asked “is this an educational tool or is it a usable tool?” This led further to potential interplay not only between the UX expert and the TFT participants, but also with the co-facilitators, to help identify the aspects of the trainings where the process tends to be “just do these 12 steps….” and identifying how to better automate or hide those processes.
Preparation and follow-up
The workshop underlined the importance of follow-up interactions among each TFT “ground team” (Internews, the UX designer, and the trainer, with developers once identified) to provide further operational security guidance as relevant to the country and community, as well as to enable the UX expert and the trainer to co-design the need finding interviews. We will be conducting these via calls, emails, and an on-site, pre-TFT meeting of the facilitators to iron out schedules and facilitation.


